Encryption means decoding or locking the data to protect it from unauthorized access. It makes the plaintext data an unreadable form that doesn’t make sense to the reader. The encrypted data looks like a string of random alphabets and digits. Complex mathematical algorithms and digital keys are used to encrypt data. So, for example, if you encrypt the word “happy” it will seem like “fas121sd45asdsad12sad12”. The only person having proper authorization such as a password, private key, secret code, session key, etc. can decrypt the data and read it.
So, what does encryption mean in terms of real-world applications?
Encryption is the process of converting human-readable data (plaintext) into unintelligible ciphertext. This scrambling of data is the result of an algorithmic operation that uses a cryptographic key. Simply put, encryption takes your data and makes it random enough so that anybody who steals it can’t read it unless they have the key to turn it back into a human-readable form.
Symmetric Encryption
The same key is used for both encrypting and decrypting messages. Because the entire mechanism is dependent on keeping the key a shared secret — meaning that it needs to be shared with the recipient in a secure way so that only they can use it to decrypt the message — it does not scale well. Symmetric encryption algorithms can use either block ciphers or stream ciphers. With block ciphers, a number of bits (in chunks) is encrypted as a single unit. For instance, AES uses a block size of 128 bits with options for three different key lengths — 128, 192, or 256 bits.
Symmetric encryption suffers from key exhaustion issues and, without proper maintenance of a key hierarchy or effective key rotation, it’s possible that every user can leak information that can be potentially leveraged by an attacker to reconstruct the secret key. Although there are key management issues with symmetric encryption, its faster and functions without a lot of overheads on network or CPU resources.
Pros and cons of Symmetric Encryption
The advantages of symmetric encryption are that it is easy to set up. It is pretty straightforward, all ages and backgrounds can use it.
The drawback is that the secret key needs to be shared with the recipient. In the case of PEM, the secret key is encrypted with the user password. Just make sure that the password is not easily guessed. If you use the same secret key to encrypt all your emails and if someone learns that secret key, you will compromise all your encrypted emails.
Asymmetric Encryption
Asymmetric encryption uses a pair of related keys — a public and a private key. The public key, which is accessible to everyone, is what’s used to encrypt a plaintext message before sending it. To decrypt and read this message, you need to hold the private key. The public and the private keys are mathematically related, but the private key cannot be derived from it.
In asymmetric encryption (also known as public-key cryptography or public-key encryption), the private key is only shared with the key’s initiator since its security needs to be maintained.
Pros and cons of Asymmetric encryption
The advantage of Asymmetric encryption is that it does not force the user to share (secret) keys. Therefore, removing the necessity of key distribution. Asymmetric encryption supports digital signing which authenticates the recipient identity and makes sure that the message does not tamper in transit.
The cons of Asymmetric encryption are that it is time-intensive and it requires considerably more effort. What’s more, you can send encrypted emails only if the other person has created key pairs which means the other person must be knowledgeable. Finally, if you lose your private key – you will lose it forever. The private key is irrecoverable which could create a whole series of new problems for you to deal with.
Encryption is used in many ways in real life. For example:
- All of the major search engines (like Google, Bing, Yahoo, etc.) encrypt your search queries and also the data they collect about you.
- All the third-party cloud storage platforms such as Google Drive, Dropbox, and Amazon AWS encrypt your stored data.
- Many encryption software applications are available (free and paid) in the market that offers the ability to encrypt personal files, photos, videos, contacts, wallet cards, notes, and audio recordings.
- Website owners use SSL/TLS certificates to facilitate the encryption of the data transferred between a website’s server and the website visitor’s browser.
- Software publishers use code signing certificates to encrypt the hash value of the downloadable software, drivers, and scripts to increase security.
- Companies use email signing certificates (S/MIME) or personal authentication certificates to sign and encrypt your messages in order to increase the security of your email communications
- A document signing certificate is useful for encrypting the content of files and documents.
- Organizations that fall within specific industries or handle specific types of data are subject to data privacy laws and regulations. For example, the Payment Card Industry Data Security Standards (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and General Data Protection Regulation (GDPR) all require the encryption of individuals’ protected information.
Symmetric vs Asymmetric Encryption in the Context of the SSL/TLS Handshake
When we surf the net using the insecure HTTP protocol, data travels in an unencrypted format that can easily be intercepted and stolen by anyone listening in on the network. SSL/TLS certificates are used to encrypt the communication channel between the client (web browsers like Chrome, Firefox, etc.) and the server you’re attempting to connect with so you can browse securely over HTTPS. While there are a number of steps involved in the handshake, the entire encryption process (that begins using asymmetric encryption and later switches to symmetric encryption for bulk transmission) takes only a few milliseconds.
Every time we connect to a website over HTTPS, an encrypted communication channel is established between our client browser and the server hosting the site. Here is an overview of encryption that comes into play when setting up a secured connection:
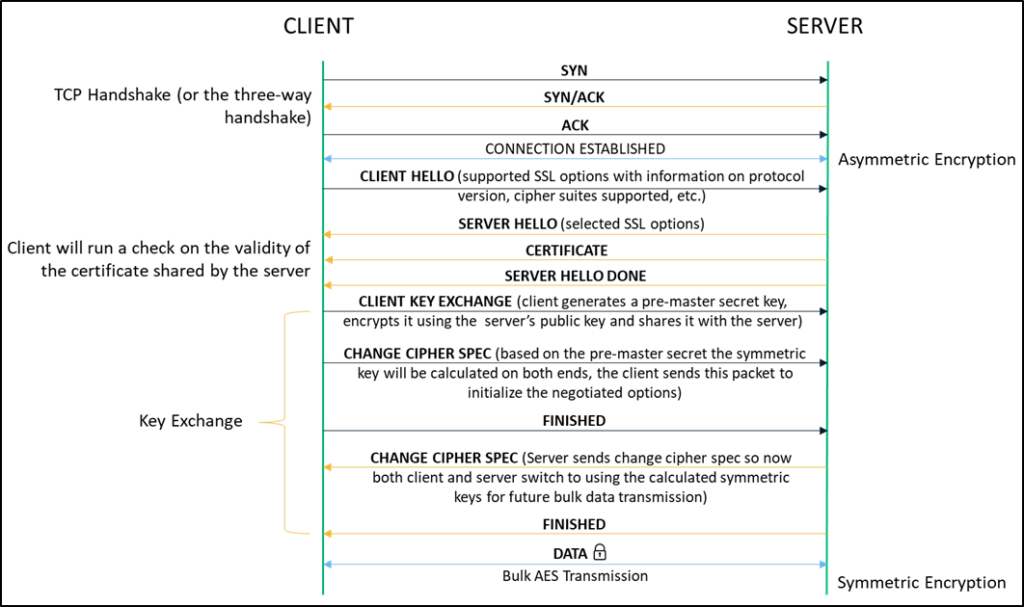
Connection Negotiation
Following the three-way handshake between the client and the server, the SSL/TLS process begins with the client hello message which, in addition to other parameters, also communicates the supported cipher suites (e.g., RSA, Diffie-Hellman, etc.).The connection is negotiated based on the highest encryption standard that is supported by both the client and the server.
Key Exchange
With the server hello message, the client receives the server’s digital certificate that holds its public key. It uses this key to generate a pre-master secret after verifying the validity of the server certificate. The client sends over the pre-master key to the server after encrypting it with the public key. The server uses the private key to decrypt and obtain the same pre-master key. The symmetric key is calculated separately by both the client and the server based on the value of the pre-master secret key.
Change Cipher Spec
After calculating the symmetric key, both the server and the client send a change cipher spec message to each other. This indicates that the remaining communication involving any bulk data transfer will be done using symmetric keys (by applying encryption standards such as AES) over a secure encrypted channel.
Happy Coding …